The DROWN attack, which stands for Decrypting RSA with Obsolete and Weakened Encryption, is a critical flaw in the SSL/TLS protocols. It exploits a server that still supports an old SSLv2 protocol, meaning an attacker can decrypt encrypted communications. This SSL vulnerability, tracked under CVE-2016-0800, exposes sensitive information such as passwords, credit card numbers, or other private data.
Although SSLv2 is very much deprecated, many servers support fallback connections or share the same key between TLS and SSLv2, putting them at risk for this type of attack.
What is the DROWN Attack?
The DROWN vulnerability occurs when a server or service:
- Enables SSLv2, which is an outdated and insecure protocol.
- Shares RSA private keys between current and old protocols.
The attacker takes advantage of this vulnerability by opening SSLv2 connections and doing some form of cryptographic operation to decrypt encrypted traffic that is secured using current versions of TLS. The attack can potentially compromise millions of HTTPS, email, and VPN servers.
Understanding CVE-2016-0800
The vulnerability linked with DROWN is reported as CVE-2016-0800. It signifies the dangers presented by servers that maintain support for SSLv2:
- Scope: Servers operating HTTPS, SMTPS, IMAPS, POP3S, and other protocols over SSL/TLS.
- Impact: Remote attackers can decrypt TLS-protected traffic, bypass the encryption, and gain access to sensitive information.
Why is DROWN Dangerous?
- High Attack Surface: Millions of servers are susceptible to the attack because they support SSLv2 or have certificates common to more than one service.
- Rapid Decryption: Applying recent techniques, attackers may decrypt intercepted data in under a minute.
- Exposure of Sensitive Information: The attack may divulge usernames, passwords, credit card details, etc.
How to Identify Vulnerability to DROWN Attack
Using CertPanel SSL Monitor
SSL Monitor, by CertPanel, simplifies the vulnerability detection procedure of DROWN attacks as well. Follow these:
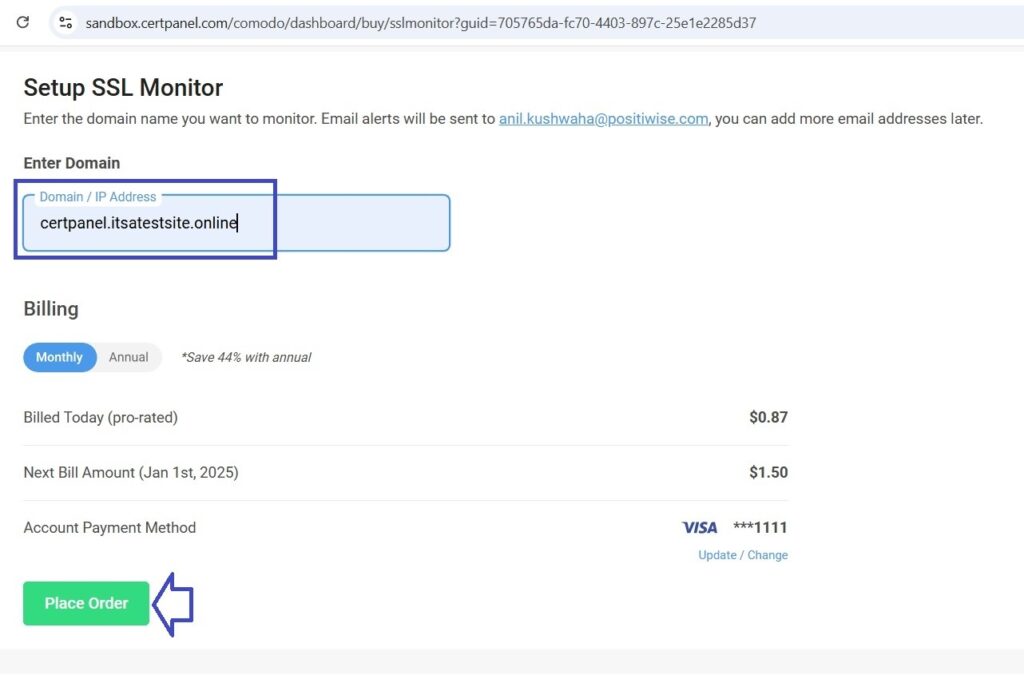
- Add Your Domain:
- Login to your CertPanel account, go to the SSL Monitor feature, input your domain, and click Scan.
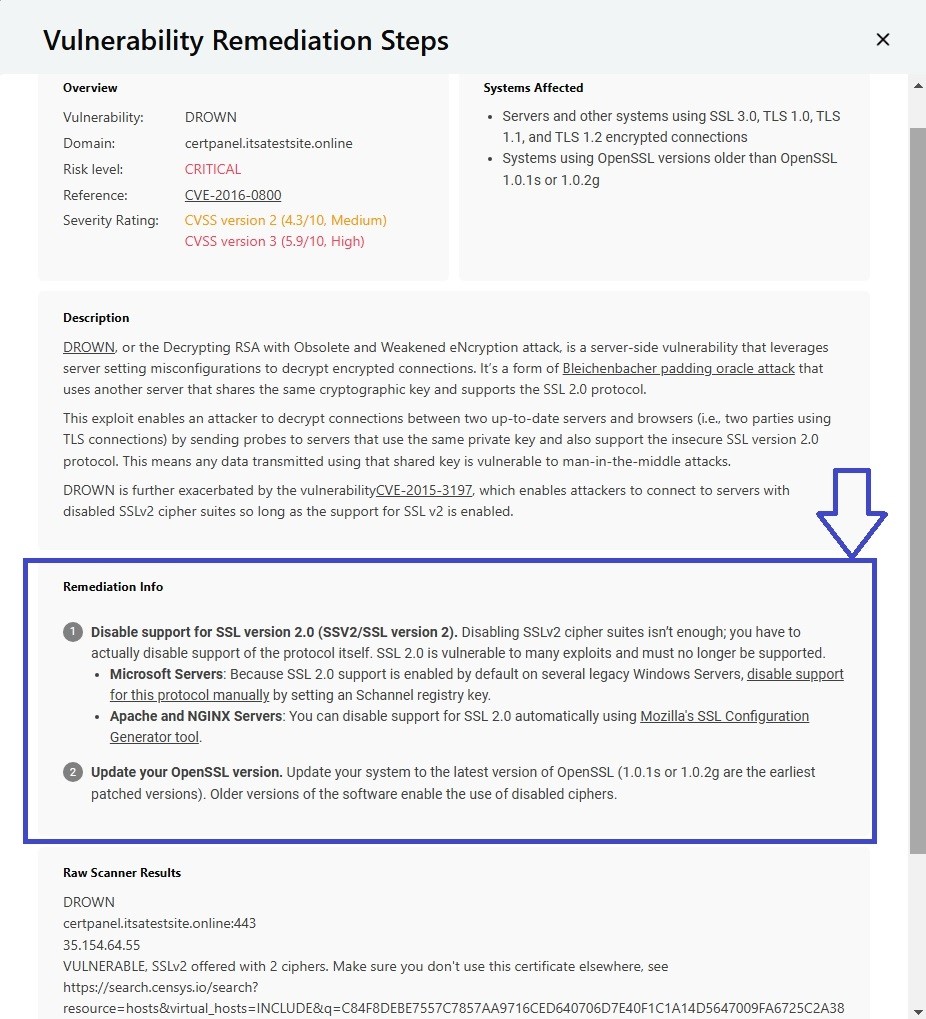
- Analyse Results:
- CertPanel generates a detailed report of your SSL/TLS configurations, including any outdated protocols like SSLv2, and provides remediation steps to fix the DROWN vulnerability.
- Set Alerts:
- Enable alerts for outdated protocols or configuration changes to address vulnerabilities proactively.

How to Fix the DROWN Vulnerability
To protect your servers from DROWN attacks, do the following steps for various server environments:
1. Windows Server (IIS)
To secure your IIS server from DROWN attacks, do the following:
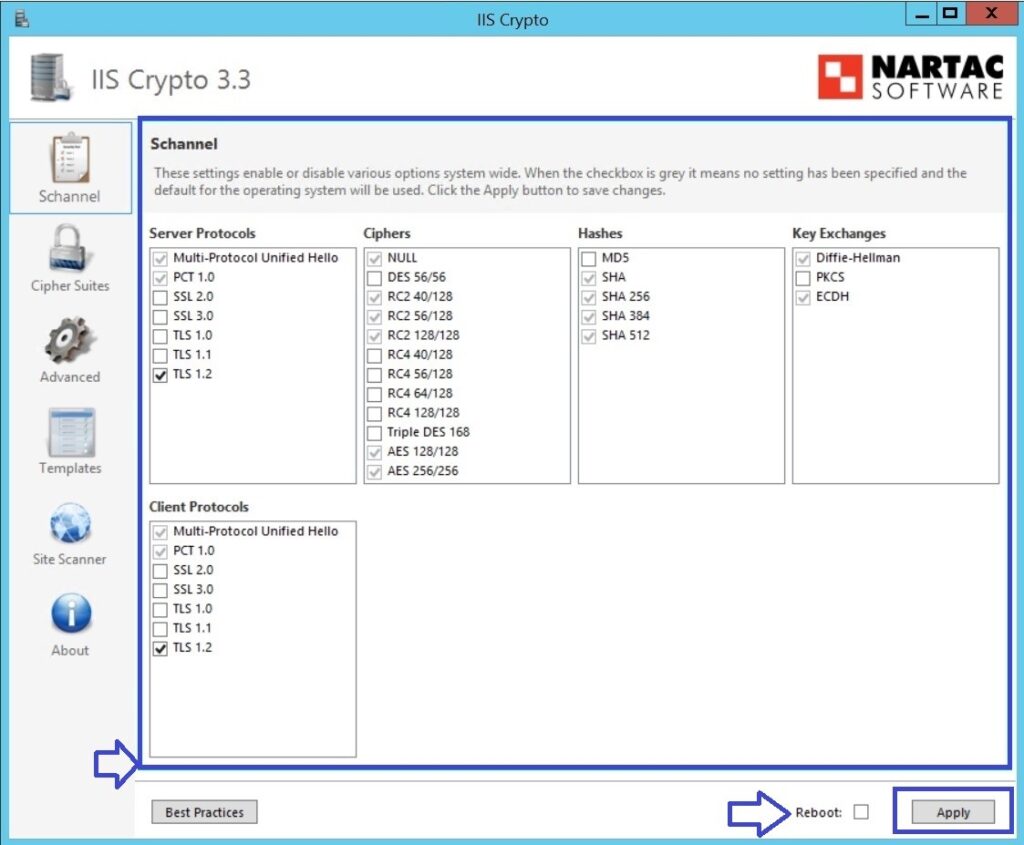
- Download and Install IIS Crypto from Nartac Software.
- Open IIS Crypto and select your server.
- In Protocols, uncheck the SSL 2.0 to deselect it and make sure TLS 1.2 is checked (you can also turn on TLS 1.3 if your environment supports it).
- Configure Cipher Suites:
- In IIS Crypto Ciphers, deselect all weak ciphers (e.g., RC4), and select only strong ciphers that are compatible with TLS 1.2 or more.
- Depending on your needs, configure FIPS-compliant ciphers (to meet certain standards).
- Click Apply.
- Restart IIS by entering the following command in a command prompt or PowerShell window:
iisreset
2. Ubuntu (NGINX)
For the protection of your NGINX server from the DROWN attack:
- Editing NGINX Configuration File: Open the NGINX configuration file:
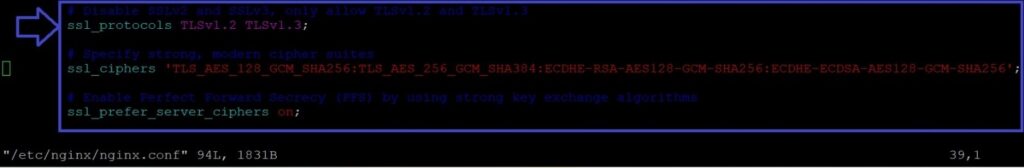
sudo vim /etc/nginx/nginx.conf- Disabling SSLv2, SSLv3, and Weak Cipher Suites: Add or modify the following lines within the server block to disable weak protocols and cipher suites:
# Disable SSLv2 and SSLv3, only allow TLSv1.2 and TLSv1.3
ssl_protocols TLSv1.2 TLSv1.3;
# Specify strong, modern cipher suites
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256';
# Enable Perfect Forward Secrecy (PFS) by using strong key exchange algorithms
ssl_prefer_server_ciphers on;
- Restarting NGINX: After making these changes, restart NGINX to apply the configuration:
# sudo systemctl restart nginx 3. CentOS (Apache)
To protect your Apache server from the DROWN attack:
- Edit Apache SSL Configuration File: Open the Apache SSL configuration file:
# sudo vim /etc/httpd/conf.d/ssl.conf - Disable SSLv2, SSLv3, and Weak Cipher Suites: Add or modify the following lines to disable weak protocols and specify secure cipher suites:
# Disable SSLv2 and SSLv3 to protect against DROWN attacks and other vulnerabilities
SSLProtocol -all +TLSv1.2 +TLSv1.3
# Specify secure cipher suites to avoid weak ciphers like RC4 and MD5
SSLCipherSuite HIGH:!aNULL:!MD5:!RC4
# Enable strong ciphers and make sure only secure options are used
SSLHonorCipherOrder on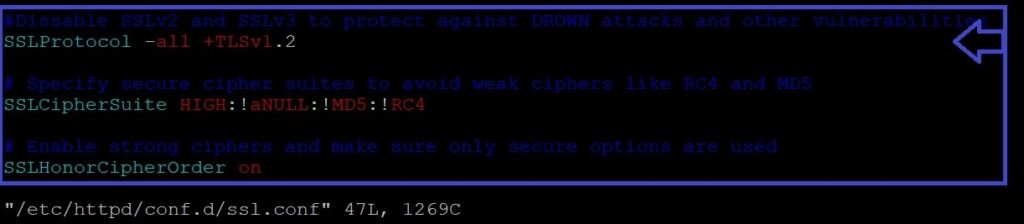
- Restart Apache: After making these changes, restart Apache to apply the new configuration:
# sudo systemctl restart httpd 4. Verify Configuration
After doing all these steps, it is very much important to check whether the SSLv2 and SSLv3 are disabled, as well as your server is using strong ciphers:
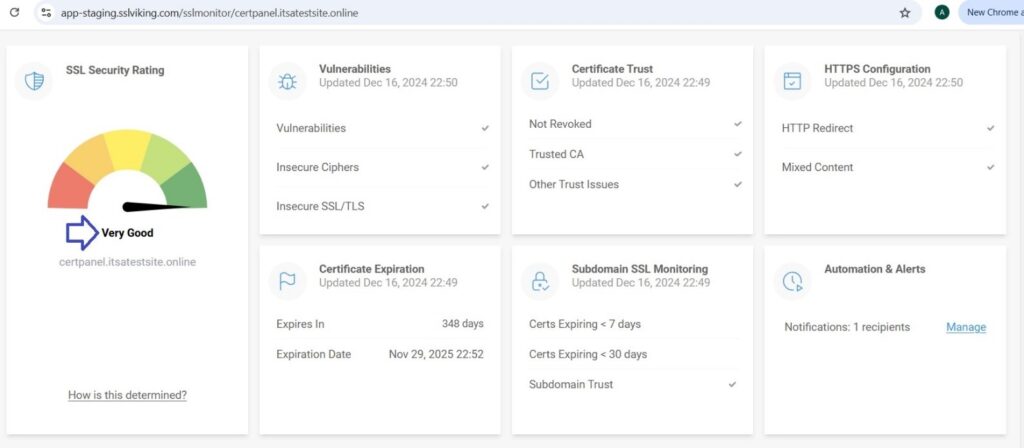
Use the CertPanel SSL Monitor to scan the server and ensure that the proper protocols and cipher suites are being used.
Key Takeaways to Avoid DROWN Attacks
- Disable Legacy Protocols: Make sure that SSLv2 and SSLv3 are disabled on all servers as the primary DROWN attack is exploiting these two.
- Use CertPanel SSL Monitor:
- Detecting Servers that are still using old and/or wrongly configured SSL protocols
- Vulnerability Reports in Detail, for fast remediation.
- Alerts Real-Time when there are issues regarding SSL/TLS.
- Ensure your servers are updated with the latest OpenSSL versions to patch vulnerabilities such as CVE-2016-0800. Regular maintenance prevents exploitation through outdated libraries.
- Enforce Modern Encryption Standards: Replace weak cipher suites with secure ones like TLS 1.2 or higher. Avoid configurations allowing cross-protocol attacks.
- Test Your Servers Regularly: Run periodic scans using tools integrated with CertPanel to ensure your systems are safe from newly discovered vulnerabilities.
The DROWN attack thus points to the need for a security best practice in maintaining SSL/TLS configurations up to date. Though the protocol is dated, its presence within server configurations still poses severe risks to millions of systems. With the use of tools such as CertPanel SSL Monitor, updated servers, and compliance with the modern encryption standard, one can protect one’s system from DROWN as well as similar vulnerabilities.
FAQs
The CertPanel’s SSL Monitor offers real-time scanning with detailed reports on SSL/TLS configurations to help detect such vulnerabilities as DROWN and raise alerts for misconfigurations for prompt action.
Disabling SSLv2 is a good starting point, but you need to update OpenSSL libraries and force strong cipher suites for all connections for complete protection.