OCSP stapling is a performance-enhancing and privacy-protecting extension to the Online Certificate Status Protocol (OCSP), which validates SSL/TLS certificate revocation status. Without OCSP stapling, browsers directly contact the Certificate Authority (CA) to verify the certificate’s status—introducing latency and potential privacy issues.
When OCSP stapling is enabled, the server attaches (or “staples”) a signed response from the CA to the SSL/TLS handshake, eliminating the need for browsers to query the CA. If misconfigured, users may see browser security warnings due to certificate revocation check failures.

How OCSP Stapling Works
- The web server periodically fetches the OCSP response from the CA’s responder.
- It caches the response locally.
- During the SSL/TLS handshake, the server includes the cached OCSP response in the handshake packet.
- The browser verifies the stapled OCSP response instead of contacting the CA.
This approach reduces response time, preserves privacy, and improves reliability.
Benefits of OCSP Stapling
- Improved Performance: Eliminates round-trip delays to the CA.
- Better Privacy: Prevents user IP addresses from being exposed to third-party CAs.
- Error Mitigation: Reduces chances of certificate revocation errors or page load failures.
How to Check OCSP Stapling
1. Check OCSP Stapling with CertPanel SSL Monitor
CertPanel’s SSL Monitor simplifies OCSP stapling verification:
- Log in to CertPanel and open SSL Monitor.
- Run a scan on your domain (e.g., wi.testroot.net).
- Check the scan results under Certificate Information.
- The OCSP Stapling field will show offered or not.
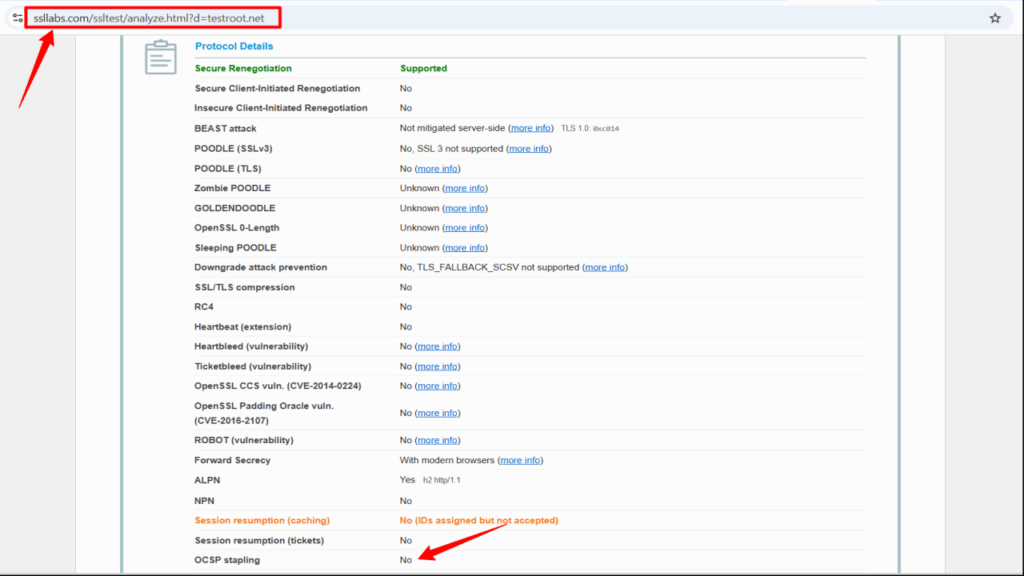
2. Check OCSP Stapling Using SSL Labs
- Go to SSL Labs SSL Test.
- Submit your domain and check the OCSP Stapling field in the results.
How to Enable OCSP Stapling on Servers
Windows Server 2022 / IIS
- Open IIS Manager > Site > SSL Settings.
- In Bindings, confirm HTTPS is selected with a valid certificate.
- Click Edit and uncheck Disable OCSP Stapling.
- Run iisreset /restart in Command Prompt.
Ubuntu 22.04 / Apache
- Open the Apache SSL configuration file:
# sudo vim /etc/apache2/sites-available/default-ssl.conf - Add the following configuration within the <VirtualHost> block:
# Enable SSL & OCSP stapling
SSLEngine on
SSLUseStapling on
# Configure Stapling Options
SSLStaplingResponderTimeout 5
# Specify bundle or full certificate chain (Root, Intermediate, and Server)
SSLCertificateChainFile /etc/ssl/certs/My_CA_Bundle.ca-bundle- Specify the OCSP cached response location must be outside <VirtualHost>:
SSLStaplingCache shmcb:/var/run/ocsp(128000) - Save the file and restart Apache:
# sudo systemctl restart apache2 Amazon Linux 2 / Nginx
- Open the Nginx configuration file:
# sudo vim /etc/nginx/conf.d/testroot.conf - Add the following directives inside your server block:
# Enable and verify OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# Configure DNS resolvers for OCSP
resolver 8.8.8.8 8.8.4.4 valid=300s;
resolver_timeout 10s;- Restart Nginx:
# sudo systemctl restart nginx Troubleshooting OCSP Stapling
- Incomplete Certificate Chain: Ensure chain.pem includes all intermediate certificates.
- Firewall Restrictions: The server must access the CA’s OCSP responder URL.
- Expired OCSP Response: Make sure the server refreshes the response before expiry.
Final Words on OCSP Stapling
OCSP stapling boosts SSL/TLS performance and privacy while minimizing revocation-related errors. CertPanel’s SSL Monitor helps you validate and maintain OCSP stapling with ease, ensuring secure and responsive web experiences for users.