Heartbleed is a security bug that was found in OpenSSL cryptographic library back in 2014. Also known as CVE-2014-0160, this bug makes it possible for an attacker to steal sensitive information like private keys, session cookies, and passwords by exploiting the Heartbeat extension in OpenSSL. Here we’ll discuss Heartbleed, how it works, and how to detect and prevent it on your server with the help of CertPanel’s SSL Monitor.
Understanding and mitigating the Heartbleed Vulnerability with SSL Monitor
Heartbleed vulnerability gives an attacker the ability to read into a server’s memory to read your confidential information, which can be further used for more attacks. Ensuring your version of OpenSSL is up to date is the best way to ensure this bug is fixed. Older Legacy systems may still use vulnerable versions, so it’s a critical issue to monitor.
Technical Details
- Affected Versions: OpenSSL 1.0.1 to 1.0.1f
- Vulnerability: Memory disclosure via heartbeat extension
- Impact: Exposure of sensitive data
Using CertPanel’s SSL Monitor To Detect Heartbleed Vulnerability
CertPanel’s SSL Monitor makes it easy to check your server for problems like Heartbleed. With just one scan, you can quickly find out if your server is in danger and take steps to protect it.
Steps to Detect Heartbleed:
- Sign up for a Free Trial of SSL Monitor
- Go to CertPanel SSL Monitor and sign up for a free trial.
- Once your account is active, log in to the dashboard.

- Add Your Website or Server for Scanning
- Place Your domain or server IP in SSL Monitor Dashboard to scan your data.
- Make sure that your SSL certificates are configured correctly, and the server is accessible.
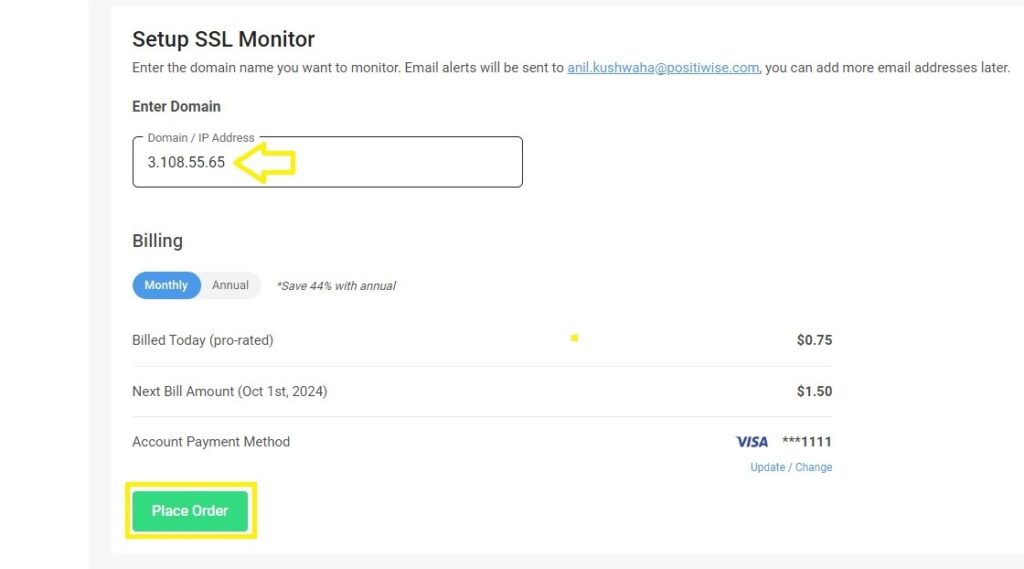
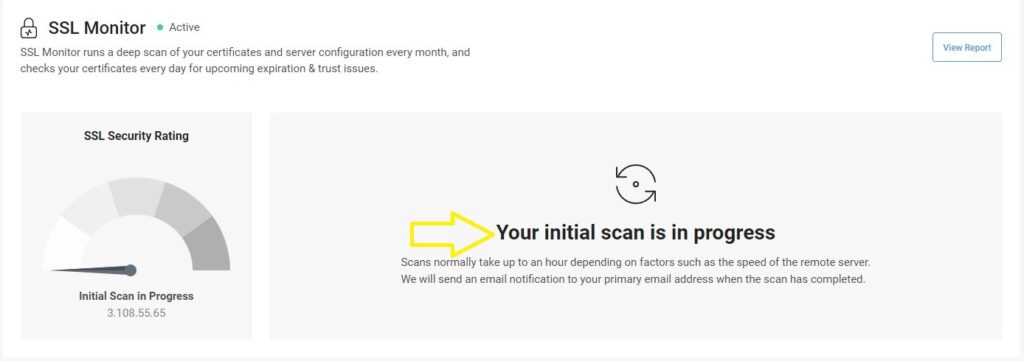
- Initiate the Scan
- Check your site with a thorough SSL scan.
- SSL Monitor will automatically scan for all known vulnerabilities, including Heartbleed.
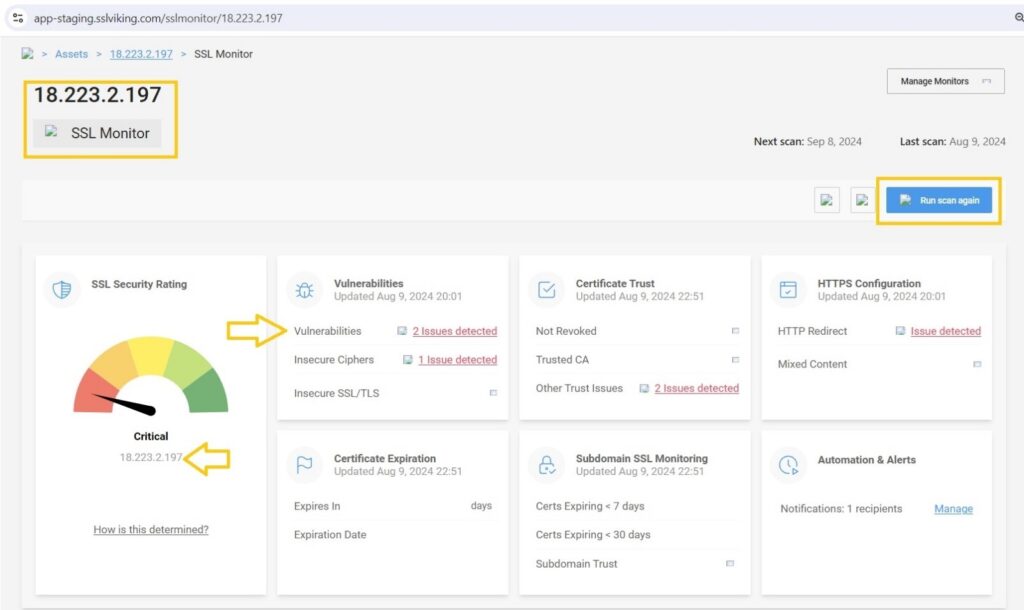
- View Scan Results
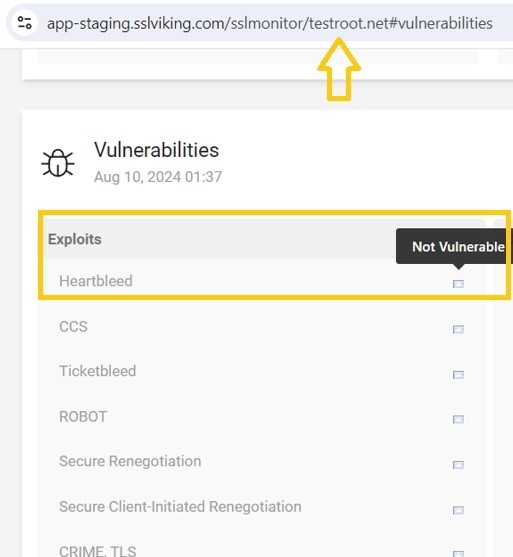
- After the scan is finished, check the results on the dashboard. If your site is at risk for Heartbleed, you’ll find detailed information about the problem, along with suggested steps to address it.
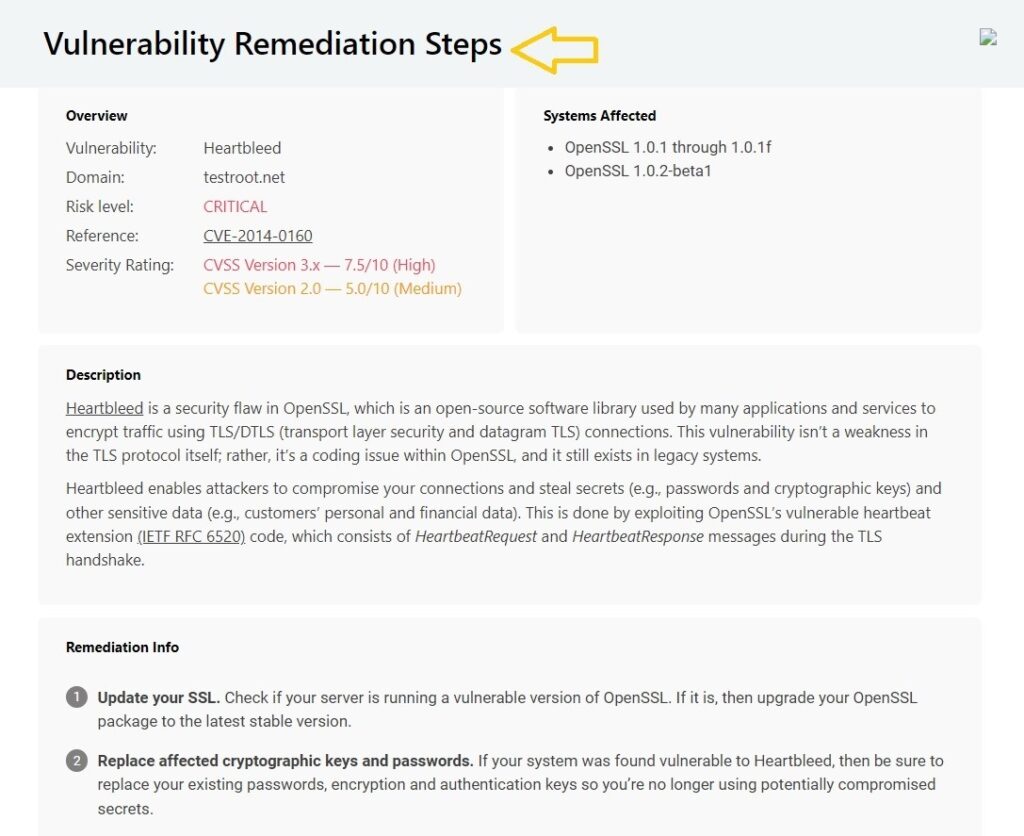
- Download and Review the Report
- Obtain the comprehensive vulnerability report that outlines the SSL/TLS configuration, and any vulnerabilities found, including Heartbleed.
- This report will indicate if the Heartbleed vulnerability is present and offer recommendations for remediation.
How to Mitigate the Heartbleed Vulnerability on Linux Servers
If SSL Monitor identifies that your server is susceptible to Heartbleed, it’s essential to address the problem right away. Follow these steps to secure your Linux server:
1. To update OpenSSL using the package manager (for modern distributions):
If your Linux distribution offers updated packages for OpenSSL, you can use the commands below to check and update your OpenSSL version:
## Verify the current OpenSSL version
sudo openssl version
## Update the package list
sudo apt-get update
## Upgrade OpenSSL to a secure version
sudo apt-get install --only-upgrade openssl
## Verify the newly installed OpenSSL version
sudo openssl version 2. For compiling and installing OpenSSL manually (for older distributions):
# Download, compile, and install the latest OpenSSL version (1.0.1g or later)
sudo wget https://www.openssl.org/source/openssl-1.0.1g.tar.gz
sudo tar -xzf openssl-1.0.1g.tar.gz
cd openssl-1.0.1g
sudo ./config
sudo make
sudo make install
# Verify the installed OpenSSL version
sudo openssl version
# Check for multiple binaries (optional)
sudo find / -name openssl
# Backup the old binary and create a symlink to the new one
sudo mv /usr/bin/openssl /usr/bin/openssl.old
sudo ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
# Verify the updated version
sudo openssl version 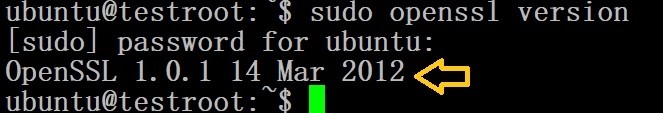
3. Restart Services
After updating OpenSSL, restart any services using the library. Typically, this includes web servers like Apache or NGINX:
sudo service apache2 restart # For Apache
sudo service nginx restart # For NGINX4. Reissue SSL Certificates
If indeed your server was Heartbleed, then do the needful i.e. reissue your SSL certificates to play it safely. This means that incorrect certificates, if any, will no longer be usable. In doing so, it that all certificates, which may have been affected, are no longer valid.
5. Rescan Your Server with SSL Monitor
After completing the fix, rescan your server with SSL monitor to make sure that the vulnerability has been fixed.
Why Use CertPanel’s SSL Monitor?
- Comprehensive SSL/TLS Vulnerability Scanning: SSL Monitor detects critical issues, such as Heartbleed, to prevent potential attacks.
- Automated Scanning: Regular automated scans can help you remain in the know about the security gaps and thus can ensure your site is adequately protected.
- Detailed Reporting: Get comprehensive reports on your server’s SSL/TLS configuration and vulnerabilities, with clear instructions on how to fix them.
Final Thoughts on the Heartbleed Vulnerability
Heartbleed is still one of the most serious SSL/TLS security flaws. Using CertPanel’s SSL Monitor, you can easily find and fix this problem, keeping your website safe from possible data leaks. Make sure your OpenSSL is current, and regularly check your servers for security issues with SSL Monitor.
Begin with a free trial of CertPanel’s SSL Monitor to make sure your site is safe from threats like Heartbleed.