Proper SSL Vulnerability Management is mostly about staying on top of the latest in technology and best practices but it’s also something that’s becoming increasingly important to monitor. That’s why there’s a growing number of tools and setups that can help handle the management workload and mitigate down-time.
In this article, we’ll explore the most common SSL vulnerabilities, discuss best practices for managing them, and introduce CertPanel SSL Scanner, a powerful tool for SSL vulnerability management. Additionally, we’ll provide practical examples of securing various server environments, including Amazon Linux with Apache, Ubuntu with NGINX, and Windows Server with IIS.
What Are SSL Vulnerabilities?
SSL vulnerabilities represent weaknesses in the implementation of the SSL/TLS protocol, configurations of the server, or the management of certificates that can be exploited by an attacker. The most common SSL vulnerabilities are as follows:
- Outdated Protocols: Use of obsolete SSL versions like SSL 3.0 or older versions of TLS.
- Weak Cipher Suites: Cipher suites with low encryption strength or vulnerable to attacks like BEAST or FREAK.
- Certificate Problems: Expired, self-signed, or not properly configured SSL certificates.
- Misconfigurations: Failure to enforce HTTPS or incorrect server settings.
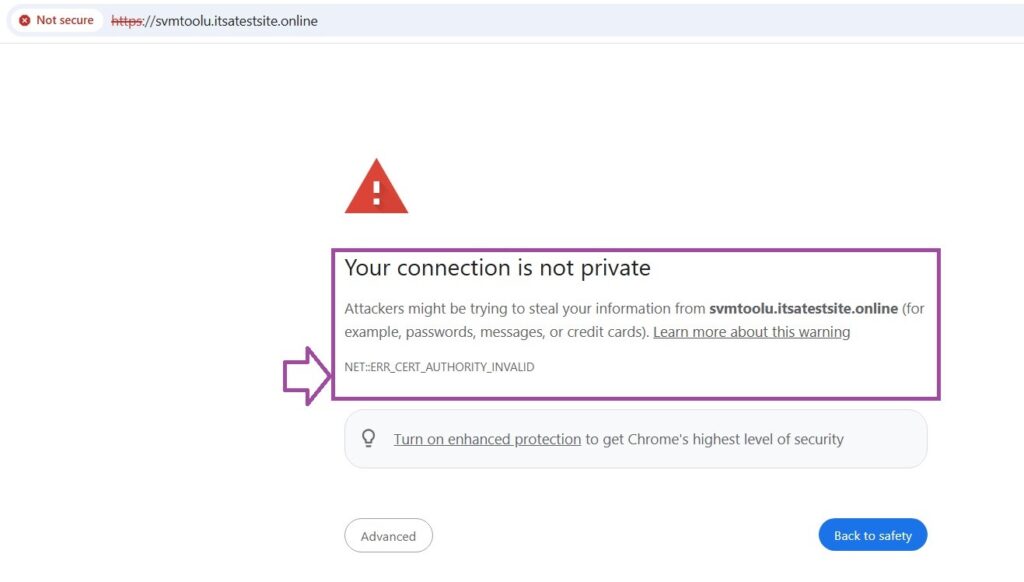
Importance of SSL Vulnerability Management
An SSL vulnerability, if not adequately addressed, causes devastating consequences that affect businesses as well as users, including:
- Data Breaches: The attackers easily intercept sensitive passwords, credit cards, and any other personal details.
- SEO as well as the Reputation Loss: Google penalises insecure websites whereas users lose the trust of having sites with SSL warnings.
- Heavy Regulatory Penalties: Non- compliance with other data protection legislation, such as GDPR, that can lead to heavy fines and penalties.
Effective SSL vulnerability management ensures your server configurations are robust, your certificates are up to date, and your site is resilient to attacks.
How to Identify SSL Vulnerabilities
Using CertPanel SSL Scanner
The process of identifying SSL vulnerabilities has been simplified through CertPanel SSL Scanner. The tool scans your website and flags weakness in cipher suites, expired certificates, and protocol-based flaws. The detailed report indicates the areas that need correction and provides recommendations with actionable improvements.
Steps for scanning SSL Vulnerability using CertPanel SSL Scanner
- Log in to your CertPanel account, go to the SSL Scanner tool, and enter the domain name.
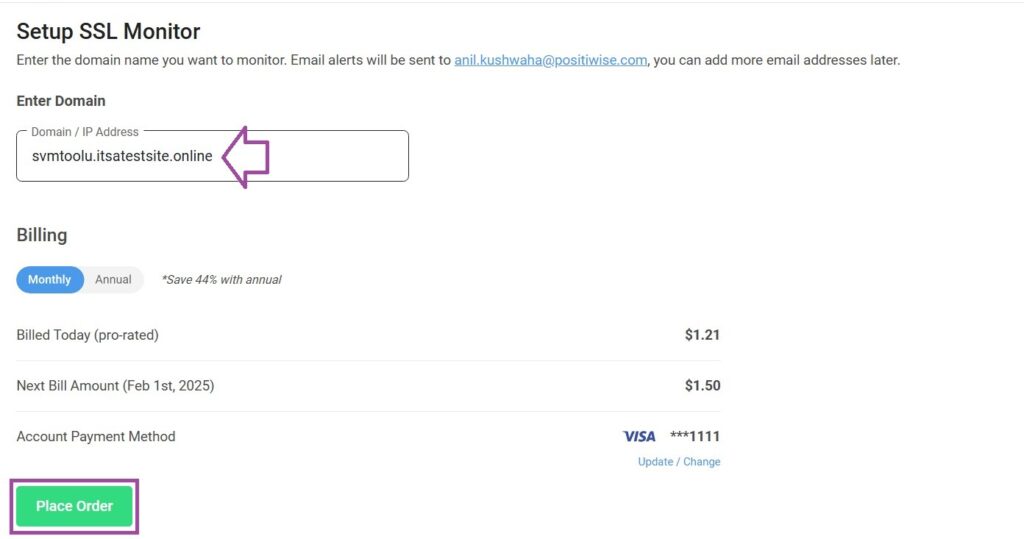
- Click Initiate Scan to start the SSL/TLS vulnerability scan for the domain.
- Go through the detailed report to know the vulnerabilities.
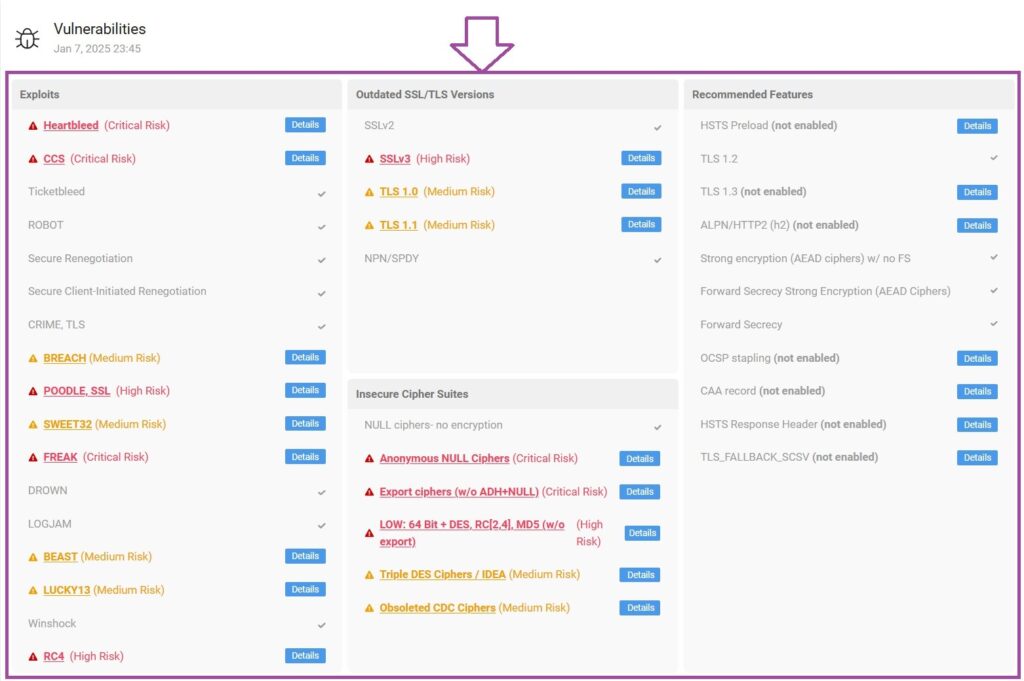
https://sandbox.certpanel.com/ and safeguard your website from possible threats.
Best Practices for SSL Vulnerability Management
- Update SSL/TLS Protocols
- Make sure your server supports only the latest versions of TLS (e.g., TLS 1.2 or 1.3).
- Disable old protocols such as SSL 3.0 or TLS 1.0/1.1.
- Use Strong Cipher Suites
- Configure your server to use secure and recommended cipher suites.
- Avoid weak ciphers such as RC4 and DES.
- Renew and Validate SSL Certificates
- Monitor your certificates for expiration.
- Use a reputable CA like DigiCert to issue certificates.
- Enable HTTP Strict Transport Security (HSTS)
- Enforce HTTPS by implementing HSTS headers to prevent MITM attacks.
- Automate Vulnerability Scanning
- Use tools like CertPanel SSL Scanner to schedule regular scans and receive alerts for vulnerabilities.
Server-Specific Configurations
1. Amazon Linux with Apache
- Update OpenSSL and Apache:
# sudo yum update openssl httpd - Enable Strong Cipher Suites:
Edit the SSL configuration:
# sudo vim /etc/httpd/conf.d/ssl.conf Add the following settings:
# Protocols - Use Only TLS 1.2
SSLProtocol -all +TLSv1.2
# Updated Cipher Suites - Exclude Weak Ciphers
SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:!CBC:!RC4:!SHA1:!3DES:!MD5:!LOW:!EXP:!aNULL:!eNULL
SSLHonorCipherOrder On 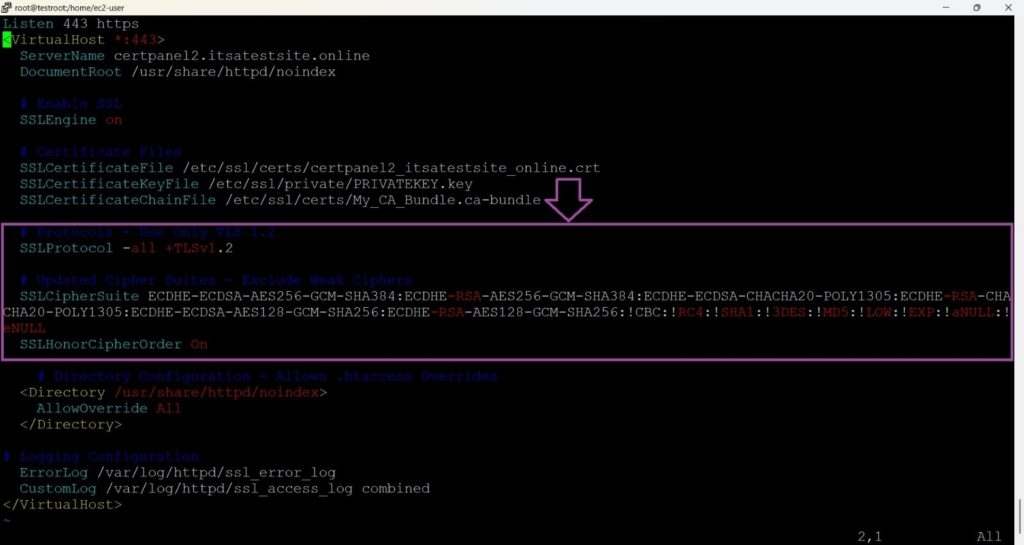
- Restart Apache:
# sudo systemctl restart httpd 2. Ubuntu with NGINX
- Update OpenSSL and NGINX:
# sudo apt-get update && sudo apt-get install openssl nginx - Configure Strong SSL Settings: Edit the NGINX configuration file:
# sudo vim /etc/nginx/sites-available/default - Add the following under the server block:
# Add SSL protocols and ciphers for stronger security (adjust as needed)
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256';
# Disable HTTP data compression (GZip/Deflate) to mitigate BREACH attacks.
gzip off;
ssl_prefer_server_ciphers on; 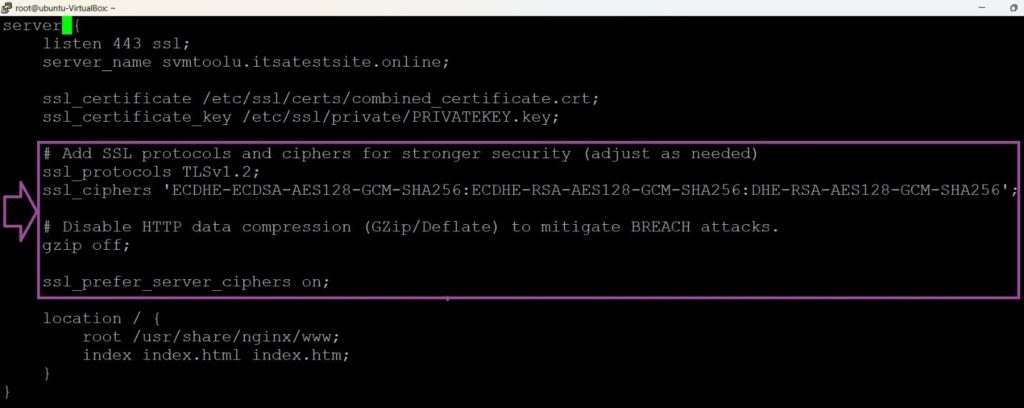
- Restart NGINX:
# sudo service nginx restart 3. Older Distributions
For unsupported distributions, first manually update OpenSSL to make sure it’s up to date and secure:
For unsupported distributions, update OpenSSL manually:
# wget https://www.openssl.org/source/openssl-1.0.1g.tar.gz
# tar -xzf openssl-1.0.1g.tar.gz && cd openssl-1.0.1g
# ./config && make && sudo make install
# sudo mv /usr/bin/openssl /usr/bin/openssl.old
# sudo ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
#sudo apt-get install --reinstall libssl1.0.0 -y
# sudo reboot4. Windows Server with IIS
- Download and Run IIS Crypto:
- Download from IIS Crypto’s website and run it as an administrator.
- Best Practices:
- Click “Best Practices” to turn off SSL 3.0, TLS 1.0, and on TLS 1.2, as well as secure cipher suites.
- Customize (Optional):
- Adjust protocols and ciphers as needed, prioritizing stronger ciphers like AES256-GCM.
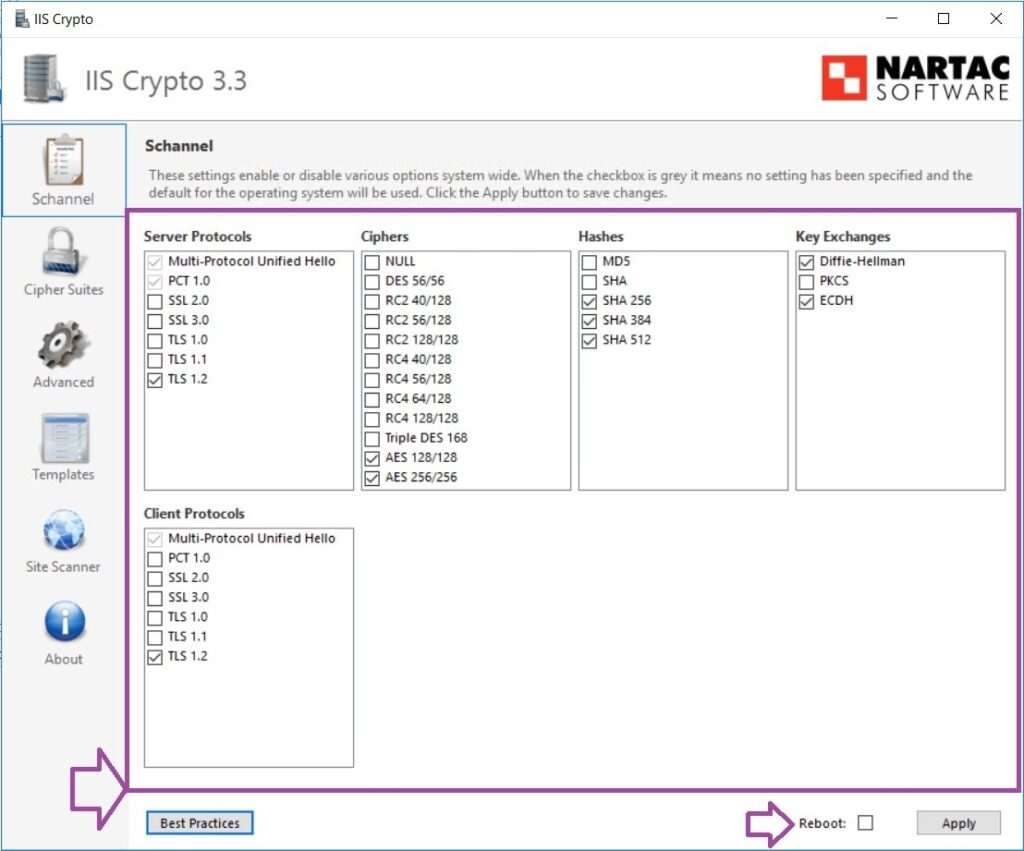
- Save and Reboot:
- Click “Apply” to save the settings and reboot the server to apply the changes.
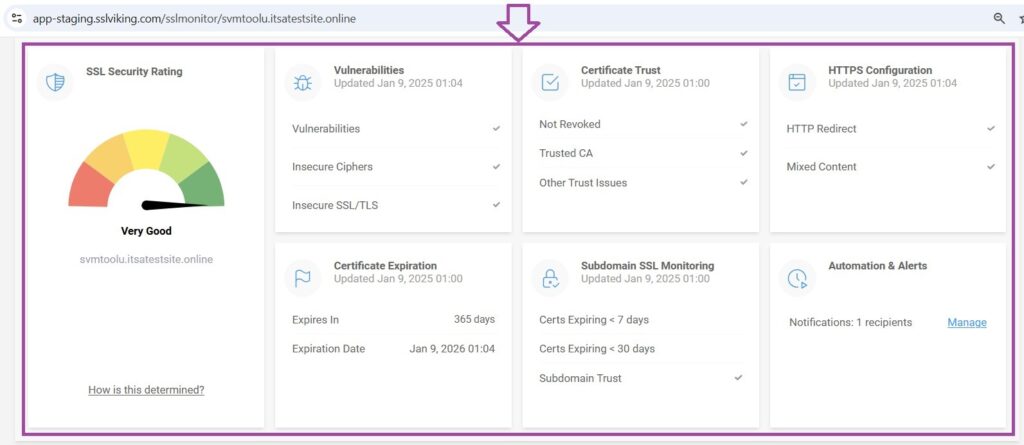
Verification Report: All Servers Secured
After applying the security measures, scans with CertPanel SSL Scanner confirm that all servers CentOS, Ubuntu and Windows Server are now vulnerability free.
Why Use CertPanel SSL Scanner?
CertPanel SSL Scanner is an easy-to-use, automated way to manage your SSL vulnerabilities. Its features are as follows:
- Full Scans: Finds weak ciphers, outdated protocols, and certificate problems.
- Detailed Reports: Offers actionable advice for how to fix those vulnerabilities.
- Real-Time Alerts: Keep you abreast of new ones.
Sign up now for your free trial of CertPanel SSL Scanner and gain control over your SSL security today.
Learn more about CertPanel SSL Scanner.
Conclusion
Managing SSL vulnerabilities is critical in protecting your website and its users from the security threats involved. You will be able to ensure robust configurations for your server by using tools such as CertPanel SSL Scanner along with best practices.
Protect your site today! Click here to sign up for CertPanel SSL Scanner for secure SSL/TLS setup.