The Logjam attack exploits weak 512-bit Diffie-Hellman (DH) key exchanges in SSL/TLS encryption. Such a weakness allows attackers to downgrade encryption and intercept or alter sensitive data. Learn how you can protect your server from the Logjam attack and secure your online communication.
What is the Logjam Attack?
The Logjam attack, CVE-2015-4000, exploits the servers that use weak 512-bit DH key exchanges. An attacker can easily downgrade encryption, making it easier to intercept or decrypt traffic. If your server uses weak encryption, an attacker can access login credentials and credit card details.
Why is the Logjam Attack a Problem?
The Logjam attack allows attackers to:
- Intercept sensitive data like passwords or payment details.
- Inject malicious data in encrypted communications.
- Degradation of security on SSL/TLS connections.
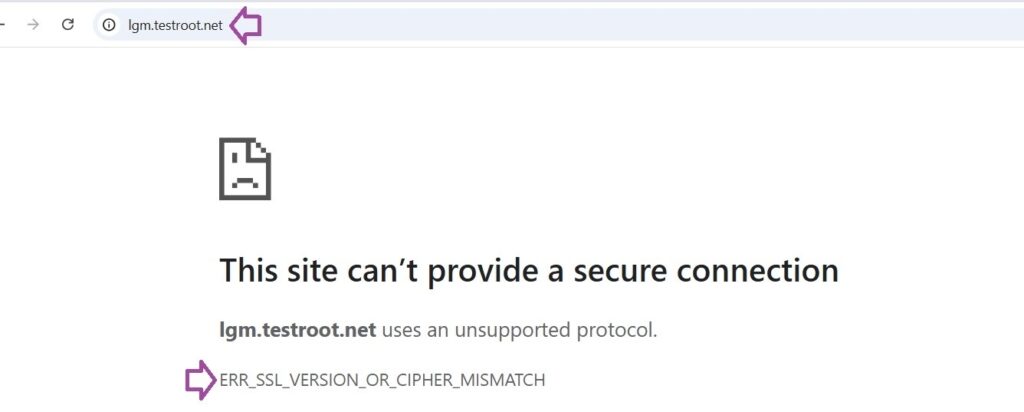
Best Practices to Prevent the Logjam Attack
To prevent the Logjam attack on your server, follow these best practices:
1. Disable Weak 512-bit Diffie-Hellman Key Exchanges & Use Stronger Encryption Algorithms
You need to disable weak encryption and enforce stronger encryption algorithms.
For Ubuntu/NGINX:
- Edit /etc/nginx/nginx.conf:
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'HIGH:!aNULL:!MD5';
ssl_ecdh_curve secp384r1;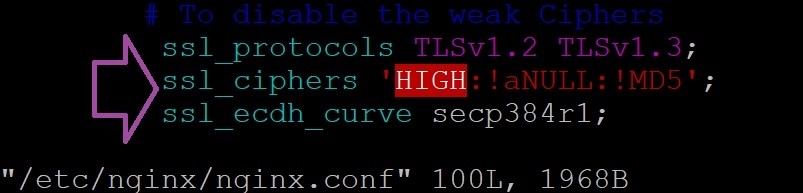
- Restart NGINX:
# sudo systemctl restart nginx For CentOS/Apache:
- Edit /etc/httpd/conf.d/ssl.conf:
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite HIGH:!aNULL:!MD5
SSLHonorCipherOrder on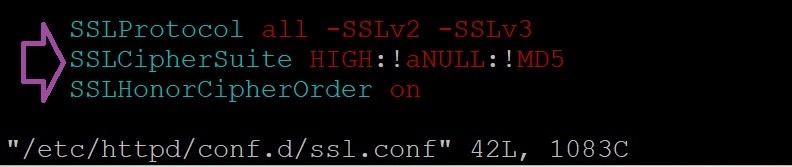
- Restart Apache:
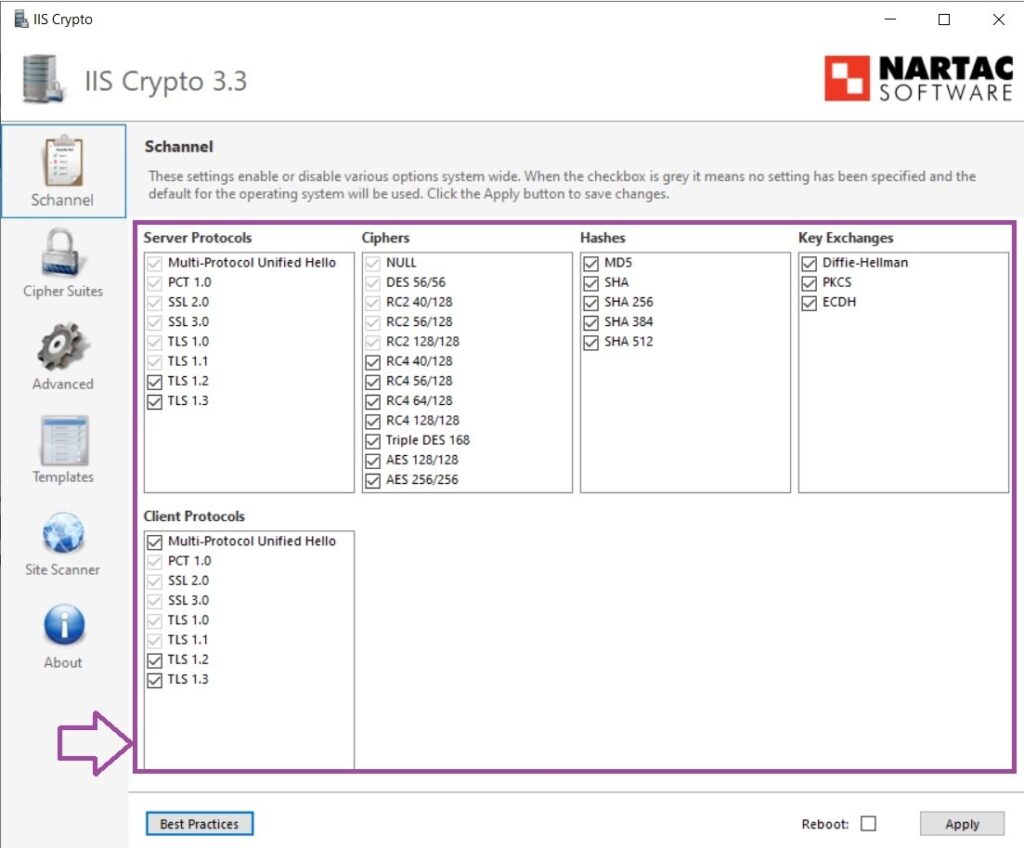
# sudo systemctl restart httpd Updated Step for Windows Server/IIS (Using IIS Crypto)
- Download and Install IIS Crypto: Download the tool from Nartac Software and install it.
- Run IIS Crypto as Administrator:
- Uncheck weak ciphers and protocols (for example, 512-bit DH, SSL 2.0, SSL 3.0).
- Enable strong options like TLS 1.2 and ECDHE under Key Exchange.
- Apply Changes: Save and reboot the server if prompted.
- Verify: Use the CertPanel SSL Monitor to scan and verify the fixes.
2. Update Your Systems
Regularly apply patches to keep your server secure against known vulnerabilities like Logjam.
How to use CertPanel SSL Monitor for security
CertPanel SSL Monitor is an easy tool to use that monitors the SSL/TLS configuration on your website for vulnerabilities like Logjam. Here’s how you can use it to keep your server safe:
How to Use CertPanel SSL Monitor to Stay Secure
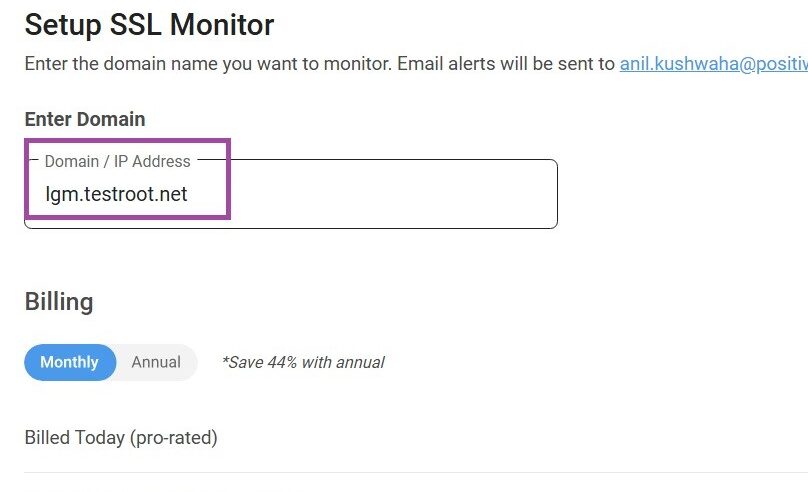
- Add Domain to CertPanel SSL Monitor: Login and add your domain to start monitoring.
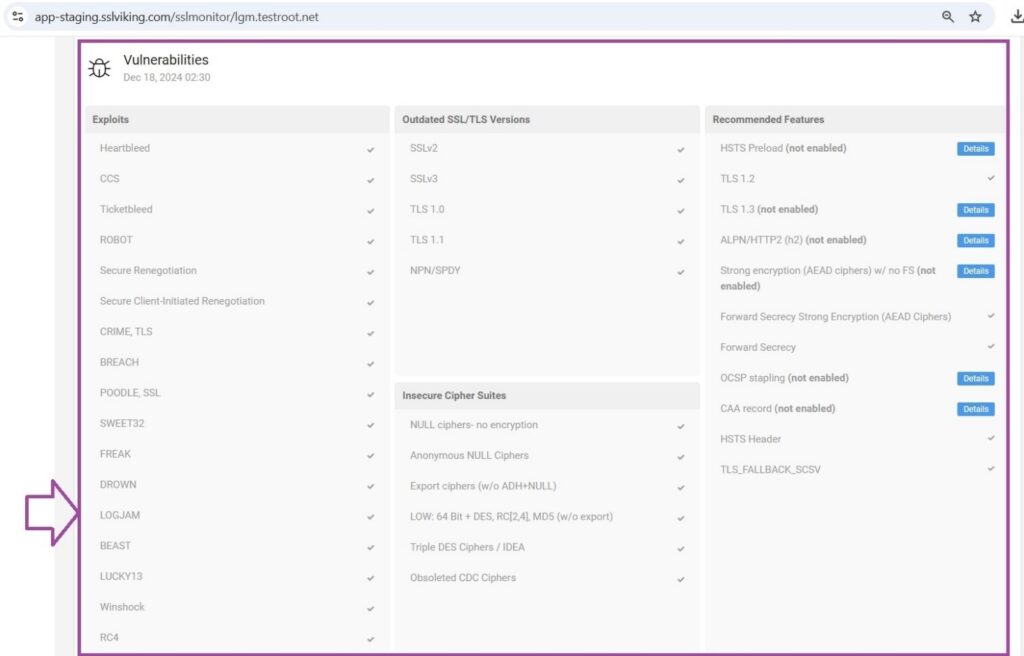
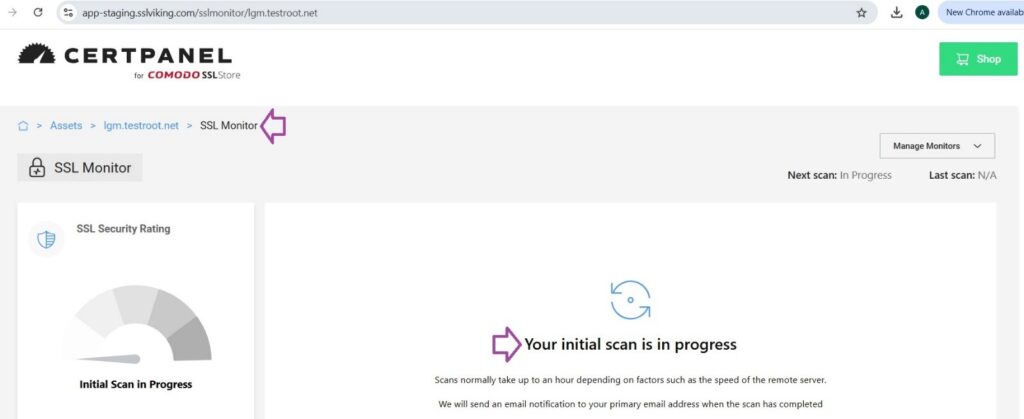
- Begin SSL Scan: Scan for vulnerabilities, including Logjam.
- Fix Problems & Re-scan: Follow the remediation steps from CertPanel to address vulnerabilities
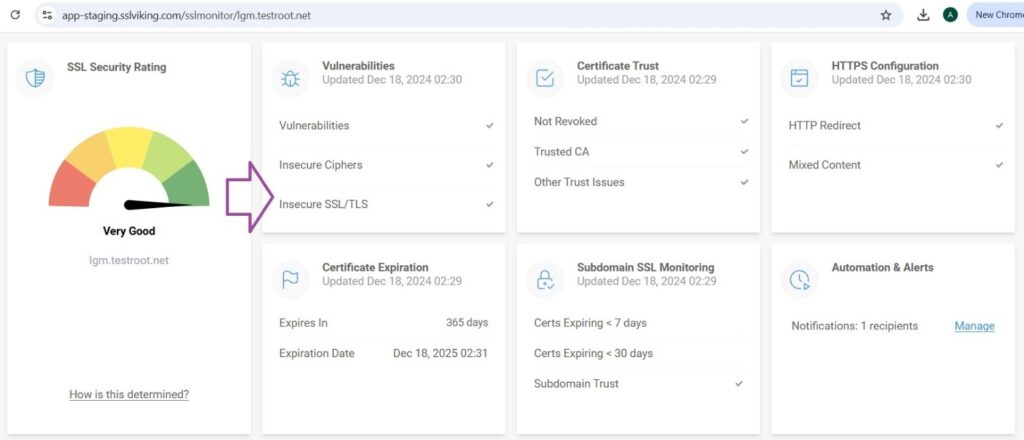
Using CertPanel SSL Monitor regularly will keep your server safe from the Logjam vulnerability and ensures that all communications are secure.
Follow these best practices and using CertPanel SSL Monitor, your server becomes secure against the Logjam attack, and your communication will be safe. So, disabling weak ciphers, enforcing stronger encryption algorithms, and keeping systems up to date are essential to mitigate the vulnerability of Logjam.