The OpenSSL Heartbleed bug, also known as CVE-2014-0160, is one of the most serious security vulnerabilities that have been detected in the OpenSSL cryptographic library. This bug, found in 2014, allows an attacker to read sensitive data from server memory such as passwords, session cookies, and private keys. This gives attackers access to private information and other serious security breaches. In this post, we will see how OpenSSL Heartbleed vulnerability works and how it is detected and fixed by the use of CertPanel’s SSL Monitor.
Overview of Heartbleed Vulnerability
- CVE-ID: CVE-2014-0160
- Affected Versions: OpenSSL 1.0.1 to 1.0.1f
- Vulnerability: Memory disclosure via Heartbeat extension
- Impact: Exposure of sensitive data, such as passwords, private keys, and session cookies.
Detection of OpenSSL Heartbleed Vulnerability
You can use CertPanel’s SSL Monitor to see whether your server is vulnerable to OpenSSL Heartbleed. This tool identifies vulnerabilities in your SSL/TLS configuration and guides you through the remediation process.
Steps to Scan for OpenSSL Heartbleed Vulnerability
- Sign Up for SSL Monitor & Configure Your Domain: Signup for a free trial of CertPanel’s SSL Monitor, activate your account, and add your server domain or IP address to start scanning.
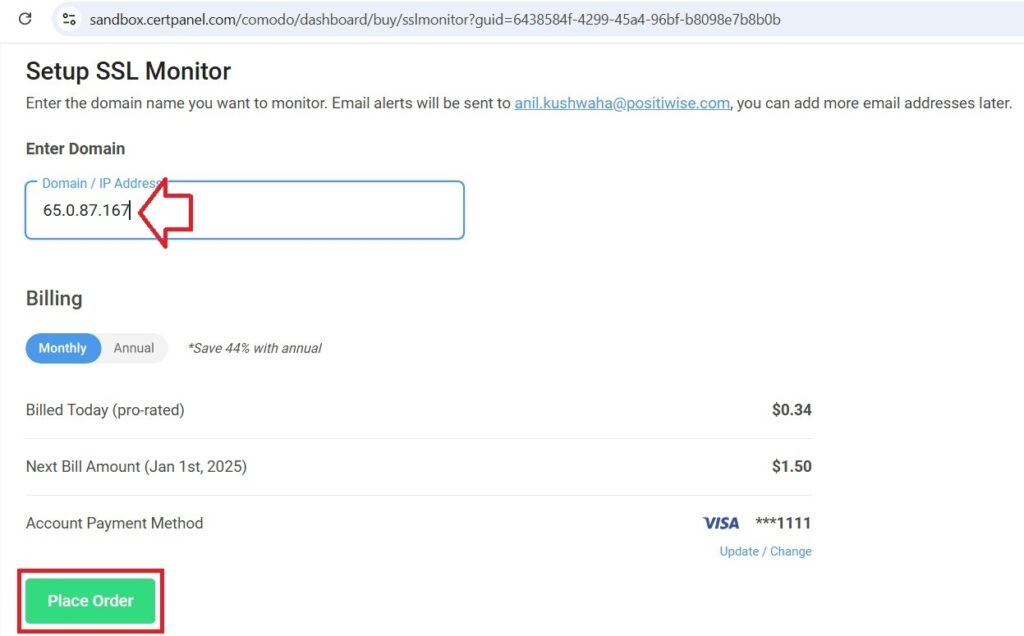
- Start the Scan: Start a scan to identify SSL/TLS vulnerabilities like OpenSSL Heartbleed issues and get a detailed report.
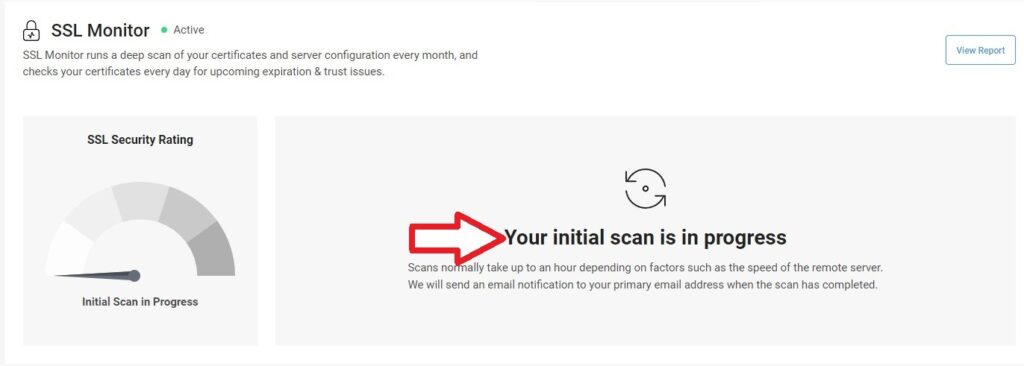
- View the Results & Download Report: Check your dashboard results after the scan. Download a detailed report with steps, if the OpenSSL Heartbleed vulnerability is found out and secure your server accordingly.
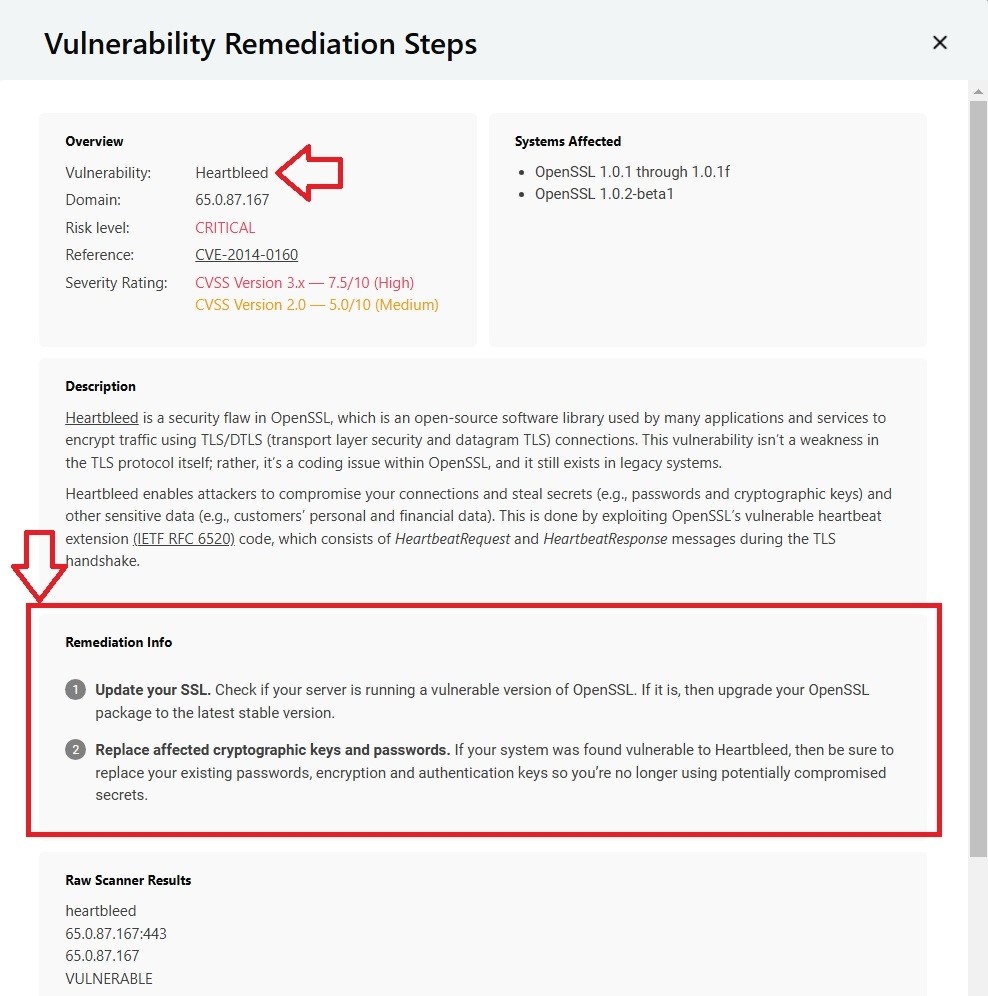
How to Fix the OpenSSL Heartbleed Vulnerability
If CertPanel’s SSL Monitor finds your server to be vulnerable to OpenSSL Heartbleed, follow the following steps to fix this vulnerability:
1. Update OpenSSL on Your Server (Linux)
For Ubuntu/Debian (newer distributions), update OpenSSL via the package manager:
For Ubuntu/Debian:
# sudo apt-get install --only-upgrade openssl
# sudo apt-get update
# sudo openssl version (Verify the version)For CentOS/RedHat (newer distributions), update OpenSSL via the package manager:
For CentOS/RedHat:
# sudo yum update openssl
# sudo openssl version (Verify the version)For older distributions, manually compile and install a newer version of OpenSSL greater than or equal to 1.0.1g:
For the older OS distributions:
# wget https://www.openssl.org/source/openssl-1.0.1g.tar.gz
# tar -xzf openssl-1.0.1g.tar.gz
# cd openssl-1.0.1g
# ./config
# make
# sudo make install
# sudo openssl version (Verify the version)- Optionally, check for multiple binaries
# sudo find / -name openssl - Backup the old binary and create a symlink to the new one
# sudo mv /usr/bin/openssl /usr/bin/openssl.old
# sudo ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl- Verify the updated version
# sudo openssl version 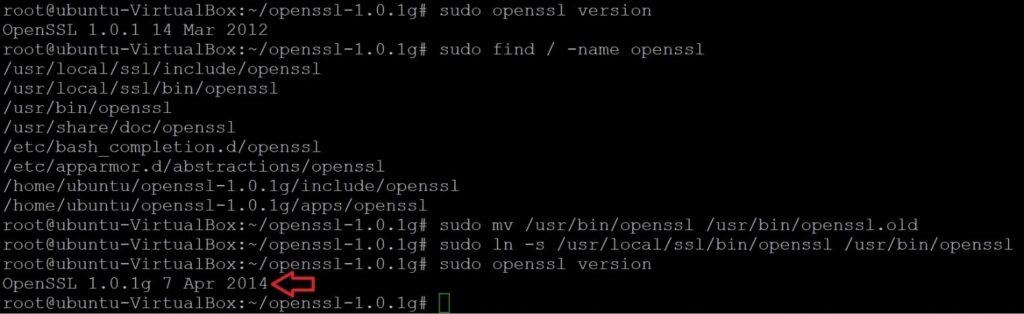
2. Reinstating a Package to resolve the Heartbleed Bug
Reinstall the vulnerable package to patch the Heartbleed bug with the following command:
# sudo apt-get install --reinstall libssl1.0.0 -y
# sudo reboot 3. SSL Monitor Re-scan for Your Server
Once done with all the required update and re-issuing of the certificates, get your server re-scanned with CertPanel’s SSL Monitor to make sure it is no longer vulnerable:
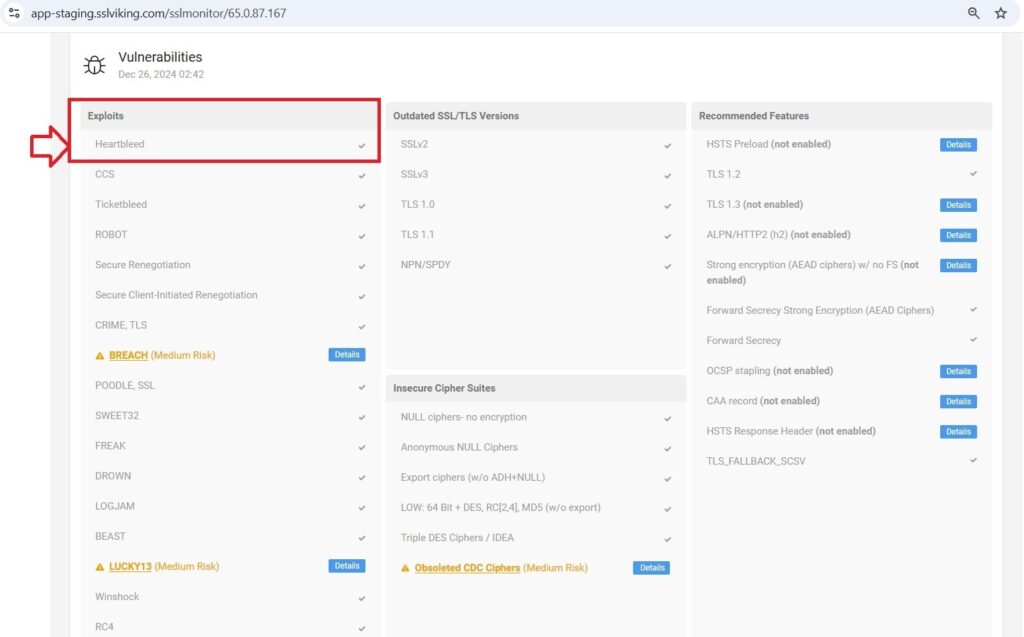
Why Use CertPanel’s SSL Monitor?
- Overall Vulnerability Scanning: CertPanel’s SSL Monitor checks for critical vulnerabilities, including OpenSSL Heartbleed, to make sure your server is safe.
- Automated Scanning: Schedule periodic scans to stay updated with any potential security gaps.
- Detailed Reporting: Obtain clear, actionable reports of the vulnerabilities and steps for remediation.
The OpenSSL Heartbleed bug is considered one of the most critical vulnerabilities affecting SSL/TLS protocols. Scanning for this vulnerability was easy using the SSL Monitor by CertPanel. Make sure your OpenSSL library is updated and keep your server safe by re-scanning servers for vulnerabilities regularly. It is also good practice to reissue the SSL certificate to protect your site against attacks.
Get Started with SSL Monitor Today
Get a free trial with CertPanel’s SSL Monitor to ensure your site isn’t vulnerable to things like OpenSSL Heartbleed.