OCSP Stapling improves SSL/TLS performance by making your Apache web server add certificate status information to the TLS handshake. This prevents clients from sending additional requests to the Certificate Authority (CA) and thus reduces latency and page load performance.
In this tutorial, we will take you through enabling OCSP Stapling for Apache on both CentOS and Ubuntu platforms and then show you how to verify the configuration using CertPanel SSL Monitor.
What You’ll Learn
- Enabling OCSP Stapling on Apache HTTP Server.
- Verifying OCSP Stapling using CertPanel SSL Monitor.
Prerequisites
Before you start:
- Your website must have a valid SSL certificate (DigiCert, Let’s Encrypt, or CertPanel).
- You must have sudo/root access to your Apache configuration files on your CentOS or Ubuntu server.
- You must have a CertPanel SSL Monitor account for verification.
Step 1: Turn On OCSP Stapling on Apache (CentOS)
To turn on OCSP Stapling on CentOS, just go through the below steps. This will boost your SSL handshakes’ speed and your security overall.
- Open the Apache configuration file for editing:
# vim /etc/httpd/conf.d/ssl.conf - Inside the <VirtualHost _default_:443> block, add the following lines:
# OCSP Stapling settings for CentOS
SSLStaplingCache "shmcb:/var/run/ocsp_stapling(128000)"
# Enable OCSP Stapling
SSLUseStapling On
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors Off- Confirm that your certificate file paths are correct:
SSLCertificateFile /etc/ssl/certs/certpanel_itsatestsite_online.crt
SSLCertificateKeyFile /etc/ssl/private/PRIVATEKEY.key
SSLCertificateChainFile /etc/ssl/certs/My_CA_Bundle.ca-bundle- Restart Apache to apply changes:
# sudo systemctl restart httpd Step 2. Enable OCSP Stapling on Apache (Ubuntu)
- Open your default.conf file in Apache:
# vim /etc/apache2/sites-available/default.conf - Add the following settings under the https block:
SSLStaplingCache shmcb:/var/run/ocsp_stapling_cache(128000)
# Enable OCSP Stapling
SSLUseStapling On
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors Off- Ensure certificate file paths are properly set:
SSLCertificateFile /etc/ssl/certs/certpanel_itsatestsite_online.crt
SSLCertificateKeyFile /etc/ssl/private/PRIVATEKEY.key
SSLCertificateChainFile /etc/ssl/certs/My_CA_Bundle.ca-bundle- Restart Apache to apply the changes:
# sudo systemctl restart apache2 Step 3. Verify OCSP Stapling using CertPanel SSL Monitor
CertPanel’s SSL Monitor offers an easy, graphical way of verifying your OCSP Stapling configuration.
- Sign into CertPanel SSL Monitor and check your domain (e.g., certpanel.itsatestsite.online).
- After scanning, go to the OCSP section of the report. Look for:
OCSP Stapling: Offered
- If it says “Not Provided” or “Revoked”, recheck your chain file and Apache settings.
- OCSP is now validated and secured. Remember to recheck after certificate renewals.
Step 4: Monitor OCSP Stapling with CertPanel
CertPanel lets you:
- Monitor OCSP status daily.
- Receive alerts on expiration or config issues.
- Auto-renew certificates and validate OCSP instantly.
For enterprises or those managing multiple sites, this automation saves time and ensures 100% coverage.
Troubleshooting
Problem: No OCSP Response in CertPanel
- Check whether your certificate supports OCSP. Free CAs sometimes don’t include it.
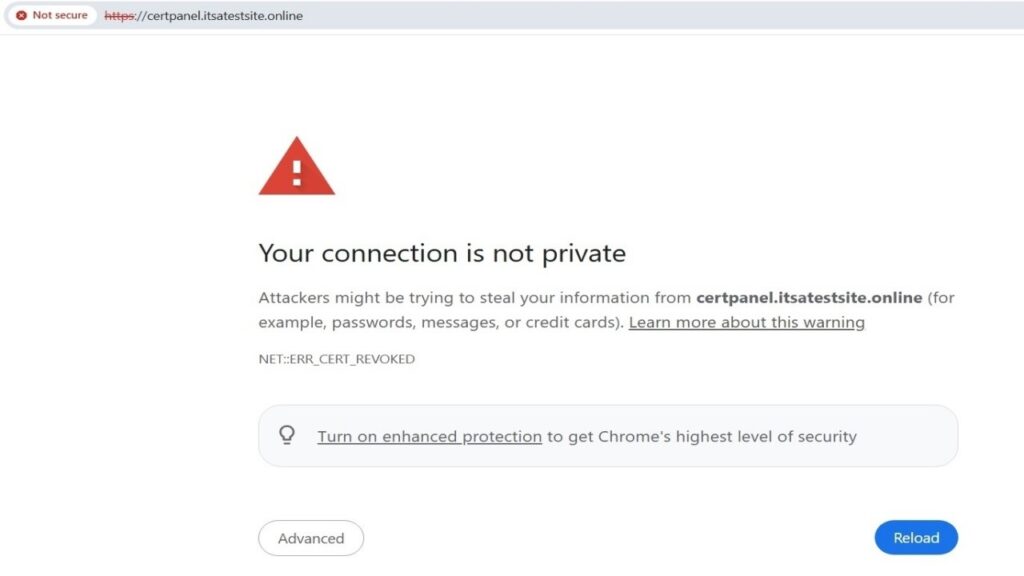
Problem: Revoked Certificate
- If a cert is revoked, the browser may show errors like “Your connection is not private.” You must replace the certificate immediately.
Final words on OCSP Stapling
Enabling OCSP Stapling boosts your site’s performance and ensures better trustworthiness. Apache provides native support, and CertPanel makes verification and monitoring painless. For modern SSL setups, this should be a default best practice.