The FREAK (Factoring RSA Export Keys) vulnerability known as CVE-2015-0204, is a major SSL/TLS security problem. It lets attackers make systems use weak encryption keys, which means they can intercept and decrypt secure communications. This article gives you a deep look at the FREAK vulnerability, shows an example of a hacked vulnerable server, and lists ways to protect your web servers. We look at how SSL Monitor from CertPanel can help spot and fix this issue.
CVE-2015-0204 Exploit Explained:
FREAK short for Factoring RSA Export Keys, influences SSL/TLS security. People found out about this weak spot this year. It puts at risk clients and servers that back RSA export-grade keys. These keys were made weaker on purpose to follow rules, but people should never use them for safe talks. Bad guys can trick a server into using these weak keys. This lets them read secret messages between the server and client.
Key Facts About FREAK Vulnerability:
- CVE ID: CVE-2015-0204
- What it Does: Allows attackers to intercept and decrypt HTTPS traffic.
- Affected Systems: Primarily affects servers and clients using vulnerable SSL/TLS configurations, particularly those that support export-grade RSA keys.
Detecting FREAK Vulnerability with SSL Monitor
Using CertPanel’s SSL Monitor, you can scan your server to identify if it’s susceptible to the FREAK attack. SSL Monitor quickly identifies weak SSL/TLS configurations, including support for export-grade RSA keys.
Steps to Scan for FREAK Vulnerability Using SSL Monitor:
- Access SSL Monitor: Go to CertPanel and activate the SSL Monitor tool.
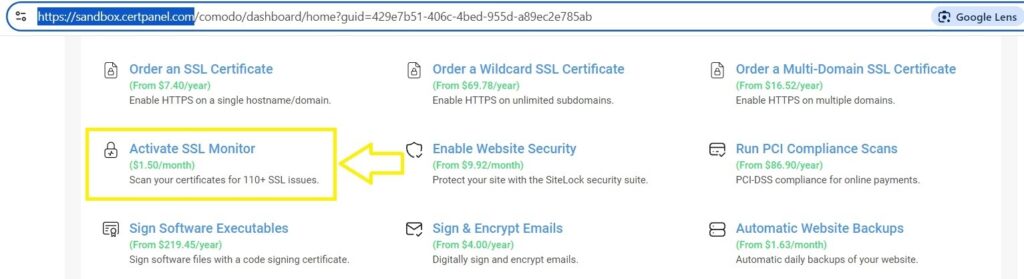
- Enter Domain or IP: Input the domain name or IP address of your server want to scan for vulnerabilities.
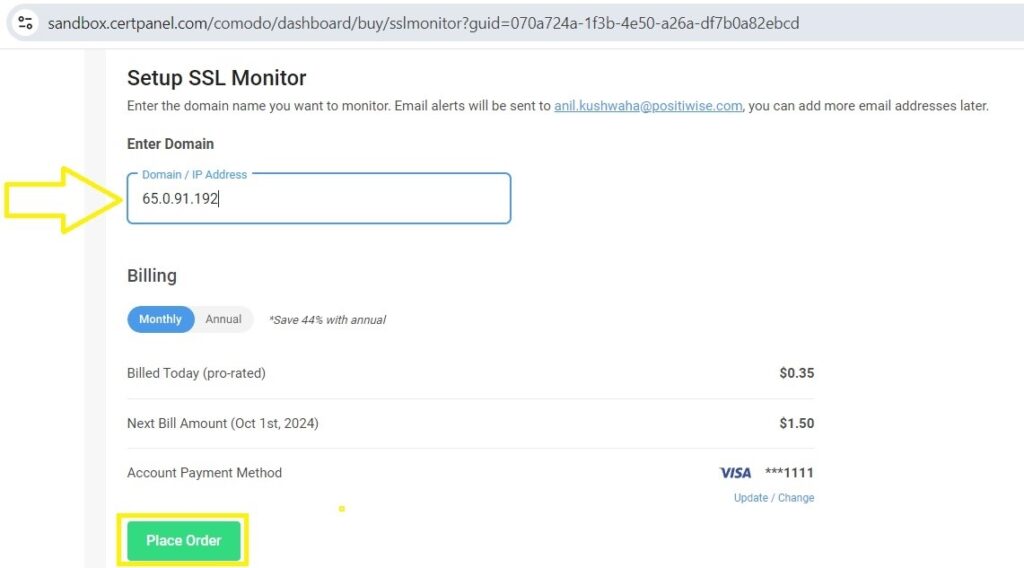
- Start Scan: Click ” Go to SSL Monitor ” to begin the Initiate Scan process. The tool will analyze your SSL/TLS configuration and report any weaknesses.
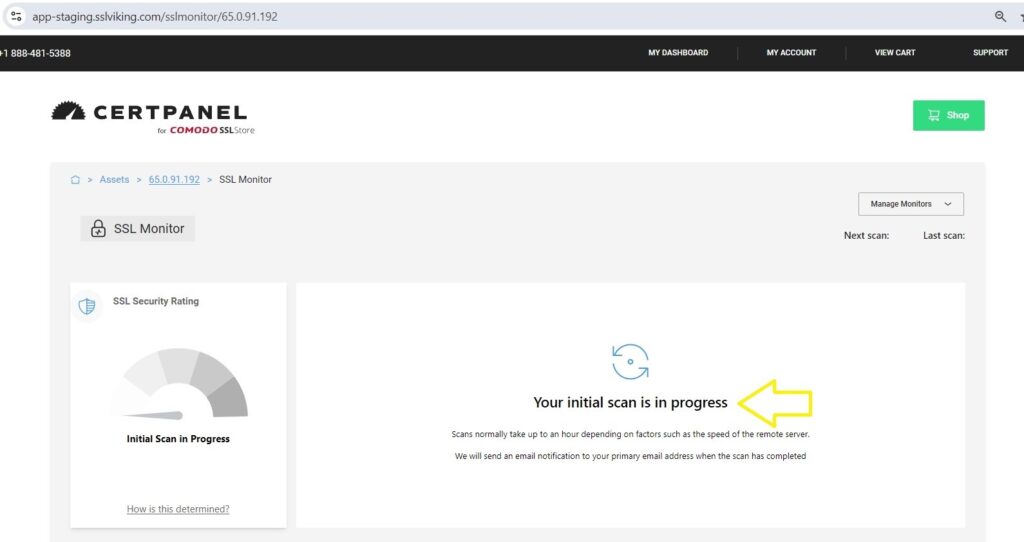
- Review Report: Check the results for any mentions of weak or export-grade RSA keys and apply the repair steps.

Mitigation Instructions for FREAK Vulnerability
To secure your server against FREAK, you need to disable support for export-grade RSA keys and ensure your server is configured to use strong encryption standards. Below are the steps for both Linux/Apache and Linux/NGINX configurations:
Linux/Apache
Step 1: Open the relevant configuration file:
Find this file at /etc/httpd/conf.d/ssl.conf or /etc/apache2/sites-enabled/default-ssl.conf.
Step 2: Change the cipher suite settings to remove weak ciphers:
Locate the SSLCipherSuite directive and modify or update it to:
SSLCipherSuite HIGH:!aNULL:!MD5:!EXPORT 
Step 3: Save the changes and restart your web server to update the new settings:
sudo service apache2 restart Linux/NGINX:
Step 1: Open the relevant configuration file:
locate the config file at /etc/nginx/nginx.conf or in the sites-available folder.
Step 2: Change the cipher suite settings to remove weak ciphers:
modify or update the ssl_ciphers directive:
ssl_ciphers HIGH:!aNULL:!MD5:!EXPORT; 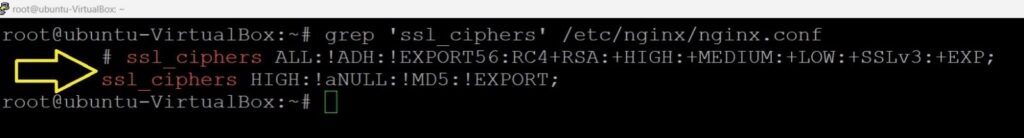
Step 3: Save the changes and restart your web server to update the new settings:
sudo service nginx restartStep 4: Run the Server Vulnerability Scanner again to check if FREAK has been fixed.
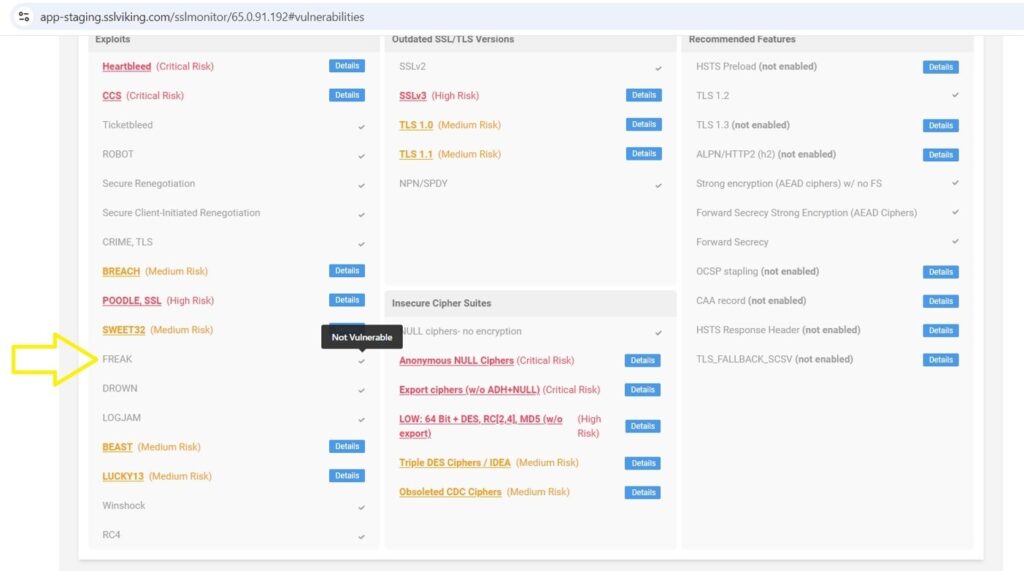
FREAK has a significant impact on SSL/TLS protocols making encrypted communications less secure. Tools like SSL Monitor from CertPanel help organizations spot these issues and take quick action to protect their servers. Follow the outlined mitigation steps for your specific server setup to ensure your environment is protected against FREAK attacks.
For a comprehensive scan of your web server’s security, try CertPanel’s SSL Monitor today and keep your site safe from known vulnerabilities like FREAK, Heartbleed, and more.
Related Articles